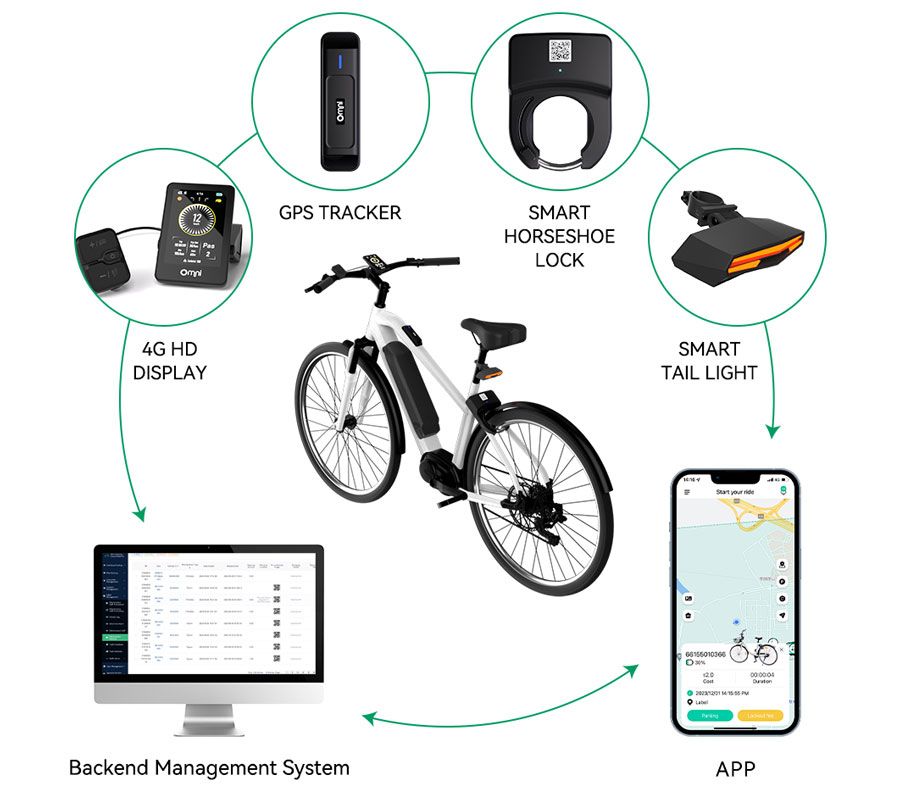
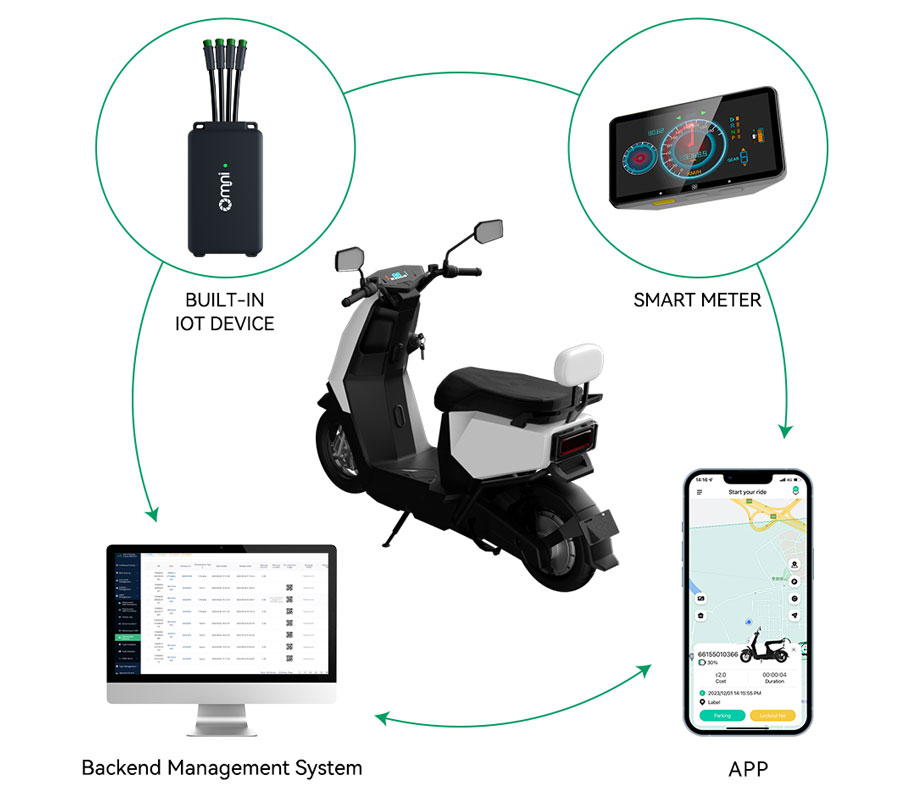
In today's tech-savvy world,Internet of Things(IoT)devices are integral to our daily lives,from smart thermostats and smart mobility such as smart micromobility to connected appliances.While most users engage with these devices for their intended purposes,there are times when developers,researchers,or tech enthusiasts want to explore the limits of these devices.This article delves into legitimate methods for overriding IoT devices,focusing on ethical experimentation and development.

Let's understand what is an IoT Devices.
IoT devices are typically designed to enhance convenience,efficiency,and automation.However,their interconnected nature can sometimes lead to unforeseen challenges,including security vulnerabilities.Understanding how these devices operate is crucial for anyone looking to experiment responsibly.
Legitimate Ways to Override IoT Devices
Firmware Modification
One of the most common methods for overriding an IoT device is through firmware modification.This involves accessing the device’s software to implement custom features or change existing functionalities.Many devices use open-source firmware,allowing developers to modify code and enhance capabilities.However,ensure that you are familiar with the device’s architecture and have the necessary programming skills.
Utilizing APIs
Many IoT devices come with official APIs(Application Programming Interfaces)that allow developers to interact with the device programmatically.By leveraging these APIs,you can create custom applications or scripts that extend the device’s functionality or alter its behavior to fit your needs.
Network Interception
Tools like Wireshark enable users to capture and analyze network traffic between IoT devices and their associated servers.By understanding the communication protocols,developers can send their own commands to the device,effectively overriding default settings or behaviors.However,use this method responsibly and only on devices you own or have explicit permission to test.
Exploiting Vulnerabilities
Security researchers often discover vulnerabilities within IoT devices.These vulnerabilities can sometimes be exploited to gain unauthorized access or control.If you’re a developer or enthusiast,participating in ethical hacking or penetration testing can help you understand how to secure these devices better while providing insights into potential weaknesses.
Default Credentials
Many IoT devices are shipped with default usernames and passwords,which users often neglect to change.This oversight can provide an entry point for overriding device settings.Always ensure to change these credentials as a first line of defense.
Ethical Considerations
While exploring the capabilities of IoT devices can be exciting and educational,it is crucial to approach this practice ethically.Only override devices that you own or have explicit permission to test.Unauthorized access to devices can lead to legal consequences and breach trust.
Overriding an IoT device can provide valuable insights and enhance your understanding of technology.Whether you’re a developer,researcher,or tech enthusiast,these legitimate methods allow for exploration while emphasizing ethical responsibility.Always prioritize security and legality in your experiments,ensuring that your actions contribute positively to the IoT landscape.




